The "NGS Approach" to Vulnerability Management
- Andy Jordan

- Mar 21, 2021
- 2 min read
Vulnerability Management Framework
For most organizations, Vulnerability Management programs have tragically been focused solely as an infrastructure or application scanning tool. However, the core purpose of a Vulnerability Management Program is to have an efficient, scalable process to identify and then remediate vulnerabilities that have been discovered. The method used to discover vulnerabilities can be through an infrastructure or application scanning technology, but it can also be identified through a monthly security update from the vendor.

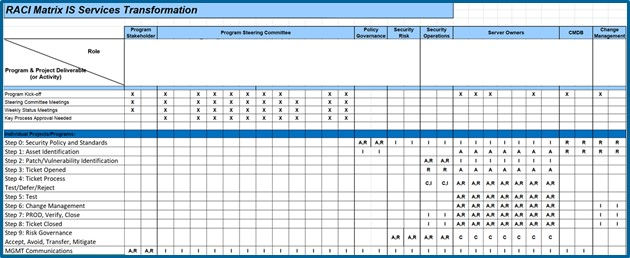
Description of Responsibilities
The table below is used as a legend to the Vulnerability Management Governance Framework listed above. Along with defining the role, it includes the overarching Vulnerability Management responsibilities.

Reducing Organizational Risk Through Vulnerability Management
The NGS Vulnerability Management program is focused on quickly remediating vulnerabilities that have already been identified through client tools. This approach allows organizations to simplify remediation plans by focusing on the activity that needs to be performed instead of focusing on CVSS and CVE scores.

Establishing a Set Customized KPIs and Metrics

The maturity of a program is built on the ability to measure the program. When NGS first engages with a client, we quickly work together to establish a customized set of metrics that can measure the vulnerability management program. The goal of each metrics/KPI is to understand how the program impacts the organization’s business objectives.
The first metric is built around understanding what the visibility the program has to the rest of the organization. Overtime, visibility should expand to ensure the program has an accurate view of the program. Below is an example of how we continue this approach to measure the how vulnerabilities are impacting the organization’s business operations.

Defining Roles and Responsibilities to Resolve Vulnerabilities
To achieve a high velocity around the timeline it takes to address vulnerabilities, we will establish a foundation for who the appropriate stakeholders and how the communication should occur during the process.
Wrap Up
Its likely that you already have a vulnerability scanner, but our hope is that this blog post has expanded the possibilities for you. We've helped transform a number of organizations using this approach and we're confident it can be a good foundation of information to help you along your journey.




Comments